Arbitrary File Delete via wsreset.exe // Bypass Adaware Antivirus
A while ago I read something about a UAC bypass method using "wsreset.exe". This method is described here https://lolbas-project.github.io/lolbas/Binaries/Wsreset/
However using this method is often flagged by anti virus software. I decided to take a closer look what wsreset.exe is actually doing and discovered something interesting: wsreset.exe can be used to arbitrary delete files. Let´s take a look at wsreset.exe and what an attacker can do with it.
wsreset.exe file description is "This tool resets the Windows Store without changing account settings or deleting installed apps". It is also auto elevated (which is already described in the UAC bypass method).
When a user opens Windows Store several cache and cookie files are created in "\AppData\Local\Packages\Microsoft.WindowsStore_8wekyb3d8bbwe\AC\INetCache". wsreset.exe simply deletes those files to clear the Windows Store cache and cookies.
Because wsreset.exe is auto elevated with high integrity (Admin rights) a local attacker can abuse the delete operation(s) to arbitrary delete files.
- First the attacker deletes the folder "\AppData\Local\Packages\Microsoft.WindowsStore_8wekyb3d8bbwe\AC\INetCookies\" The user has full control over this folder so this is no problem:
- Now the attacker creates a folder junction with "\AppData\Local\Packages\Microsoft.WindowsStore_8wekyb3d8bbwe\AC\INetCookies\" as path and the folder the attacker wants to clean (for example "C:\Windows\System32\drivers\etc") as target. This can be done by using mklink.exe with the "/J" parameter or via the powershell new-item command with the "-ItemType Junction" parameter.
- Last step is to execute wsreset.exe. wsreset.exe will follow the directory junction and delete all content in the folder configured as junction target. In this example I deleted all contents in "C:\Windows\System32\drivers\etc"
PoC - Deactivating Adaware Antivirus
When adaware antivirus is installed real time protection and the scan feature is not available:
After the user has downloaded and installed the latest (or at least some) definition/signature files, adaware antivirus provides real time protection and "protects" against threads based on the signature files.
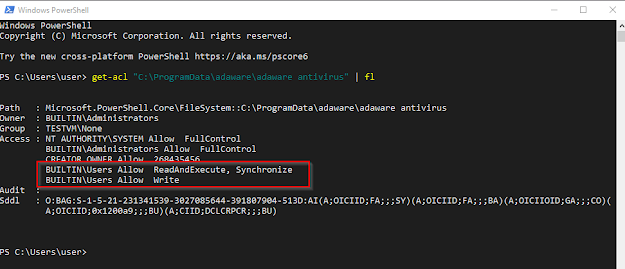
Adaware antivirus stores configuration files (and more) in the folder "C:\ProgramData\adaware\adaware antivirus". Adaware antivirus needs these files to interact with malware signatures/definitions downloaded before. Regular users cannot delete this folder:
A local attacker can use wsreset.exe to delete contents in that folder. I created a powershell function to delete the Windows Store cookie folder, create a folder junction and start wsreset.exe. Script can be found here GitHub
After running the script/deleting the folder content there are still some files/folders left in "C:\ProgramData\adaware\adaware antivirus". These files are currently opened by adaware antivirus and cannot be deleted. But this is no problem the attacker only has to wait for the next reboot because...
Adaware antivirus cannot detect any definition/signature files after the folder is cleared/partially deleted. Also a "Full Scan" or real time protection is not available. Deleting the files was also not flagged by adaware antivirus...